
A couple weeks back, Twitter experienced a widespread hack that compromised the security of every verified account on Twitter. Kanye West, Obama, and countless Internet celebrities found their accounts inaccessible, the hacker using their accounts to advertise their Bitcoin wallet, where users could send them money. This hack put things into perspective for many people, notably the fragility of their online security. If Twitter’s security became vulnerable due to working remotely, what about other workers working remotely? Are they at risk?
Yes, they are very much at risk.
The Risks Remote Workers Face
Remote workers face countless cyber-risks in their day-to-day lives, and they may not even realize it! Let’s go over a few of these risks before discussing the ways remote workers can stay safe.
1. Getting Fooled by Phishing Scams
Phishing scams are perhaps the oldest trick in the book for cybercriminals. Instead of relying on special software, phishing scams rely on social engineering, the practice of manipulating someone into committing a certain action. In the case of phishing, this action typically includes the telling of personal information, including card numbers, social security numbers, and vice versa.
Not all phishing scams are subtle (the Nigerian Prince phishing email being a prime example), but other cybercriminals play it smart and create a cohesive, compelling story. Many people fall for phishing scams every year.
2. Becoming a Victim of Data Breaches
A data breach involves a company’s systems being compromised, with hackers then stealing or releasing the once-confidential information found within. Of course, data breaches can happen outside of the workplace too, affecting people on the individual level.
Remote workers suffer the brunt of data breaches nowadays. If a remote worker were to find themselves as the “patient zero” of a data breach, they not only risk compromising their own security, but the security of the company they work—a lose-lose situation.
Ways to Keep Safe While Working From Home
Now that you know a couple of the ways you’re at risk of cybercriminals as a remote worker, let’s go over the ways you can protect yourself.
1. Being More Aware of Your Security
The tech industry has a certain piece of slang to sum up a subset of issues that risk the user’s security: PEBCAK. PEBCAK stands for “problem exists between chair and keyboard” and exists because many tech issues end up being the fault of our own.
This goes double for cybersecurity.
Try to be more aware of what you’re doing and interacting with while online. For example, be careful about what emails you click on. Minimizing human error can go a long way for your security. Below are a few ways in which you can minimize human error, as listed below.
1.1 Identifying Cloned Accounts
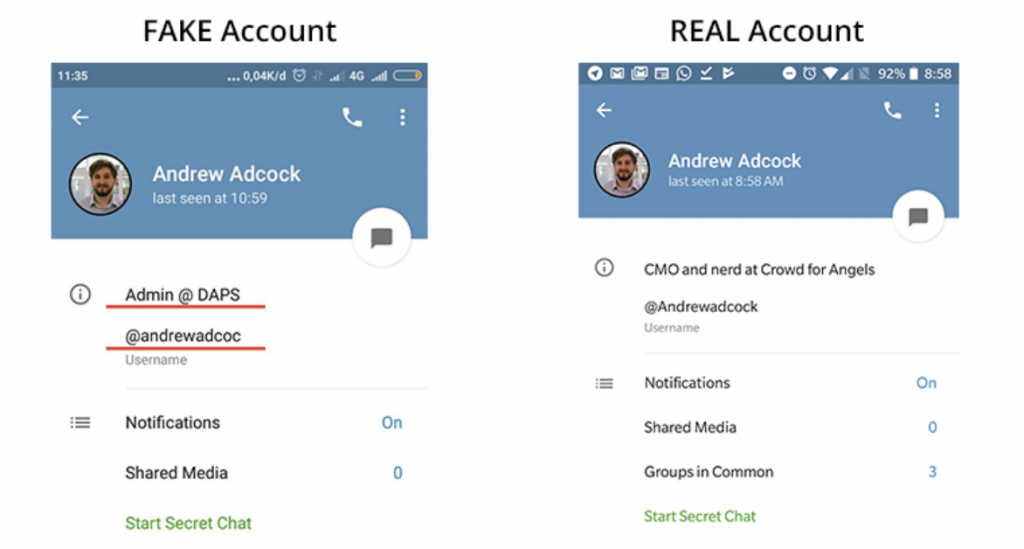
In the two images below we have a FAKE account on the left-hand side and a REAL account on the right-hand side. You should always check the person’s username very carefully for misspelling. As you can see, there is a very subtle change in the spelling of “adcock” to” adcoc” – missing the K, this slight change by the potential fraudster is a clone of a real user and an attempt to solicit information or funds.
1.2 Identifying Fake Emails
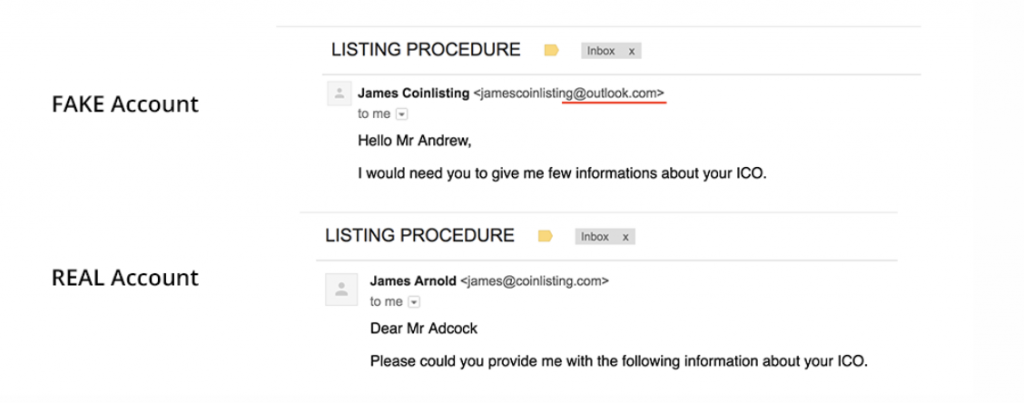
In the example below, we can see that “James”, our potential fraudster has been in touch using an email registered with Outlook.com and has mentioned the company name as part of the unique address. Sometimes this can be misconstrued because the email provider highlights the first name “James” and the last name “Coinlisting” in this case. Therefore giving the reader the impression that James is from Coinlisting. This is NOT the case, as James is using an Outlook domain and can be from anywhere!
It is also important to take a look at the language used in the email and to see if it matches your expectations of an email be received from a professional organisation.
1.3 Identifying Fake or Unrealistic Offers
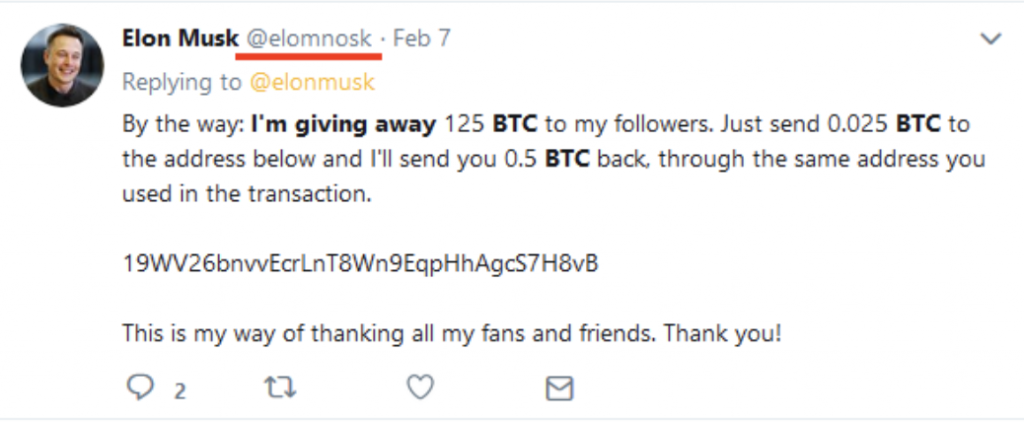
It is often said that if an offer is too good to be true, then it probably is. In the past years, there had been a wave of fraudsters posing as well as known individuals offering “FREE” cryptocurrencies, if the user first pays a small amount. This is a very common scam and is a similar to fake lotteries, items to be delivered scams and releasing funds scams. Remember, if it sounds too good to be true, it probably is.
1.4 Identify when the Scammers are using Trusted Brands
Many scams or phishing attempts include the use of well-known household brands to potentially trick the user into submitting their personal details including password, username and security information. In the example below, we can see that the ‘scammer’ has sent an email from a fake Tesco’s account before redirecting to what looks like there banking logging page.
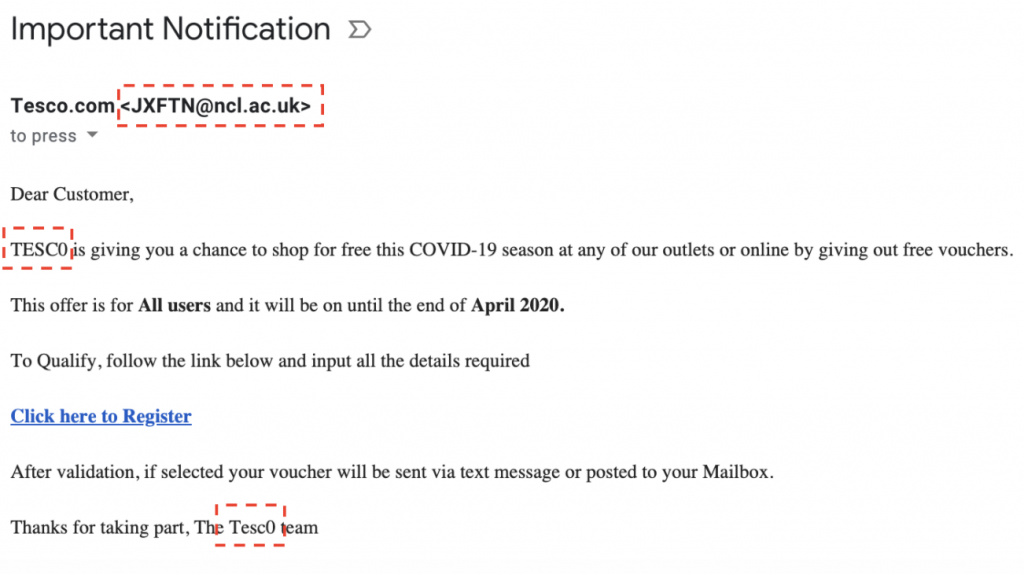
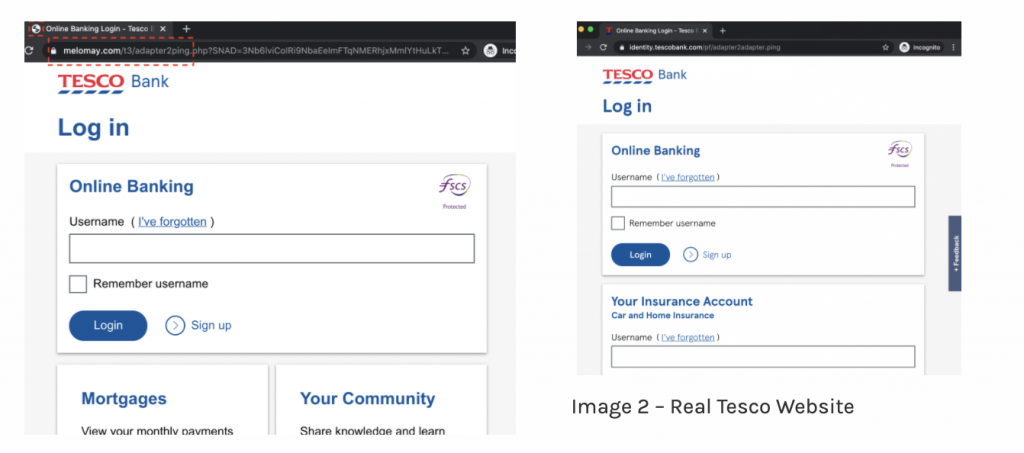
As you can see from the above images, the first thing that should ring alarm bells is the use of a domain, which is not tesco.com or tesco.co.uk instead the email has come from ncl.ac.uk. Furthermore, Tesco in this instance has been spelt with a zero (0) instead of an ‘o’.
The website that has been clicked on is very similar, the ‘scammer’ has probably copied the styles from the actual Tesco bank website. Whilst the form looks the same, not any details entered, will, in fact, be taking by the ‘scammer’. We can tell that it is a fake website by looking at the URL in the top left-hand corner. It is not taking you to tesco.com, it is instead taking you to a totally different site.
Finally, in image 2 you can see a small image in the very top corner of the browser. This is called a Favicon (https://en.wikipedia.org/wiki/Favicon) not that the fake site in image 1 does not have a favicon. All good websites, will usually have this small icon representing their brand.
2. Using a VPN for Your Network
You might think your home network is safe, but the truth is: no network is completely safe. However, that doesn’t mean there aren’t ways to secure your network further.
One way to do so is by installing a home VPN router. A VPN router would allow you to encrypt the data on your network, as well as securing all the connected devices.
We hope that the above examples have given you some information on what to look out for when communicating online and how to keep safe while working from home. If you would like to read further on how to avoid fraudsters and beware of phishing read our previous blog on the matter, here: https://crowdforangels.com/blog/avoiding-fraudsters-beware-of-phishing/
Should you wish to talk or confirm the identity of a communication concerned with Crowd for Angels, please call us on +44 (0)207 437 2413 or use our live chat function here: https://crowdforangels.com/


